Blog'as RSS Feed
0
102
Kodėl verta rinktis Work Sharp peilių galąstuvą?Ar pavargote nuo neefektyvių peilių galąstuvų? Norite aštrių peilių be pastangų? Tuomet Work Sharp – kaip tik jums.✅ Patikimumas ir inovatyvumas viename..
1
146
Reolink Home Hub ar NVR – kas geriau jūsų namų saugumui?Kai svarstote apie vaizdo stebėjimo sistemos įrengimą, kyla klausimas – kokį valdymo įrenginį pasirinkti? Tradicinį NVR (Network Video Recorder)..
0
98
Mio vaizdo registratoriai: kodėl jie tapo būtinybe šiuolaikiniam vairuotojui?ĮžangaŠiandien, kai keliuose daugėja automobilių, eismo intensyvumas ir avarijų rizika auga. Vaizdo registratoriai tapo ne ..
2
264
Reolink Go (G330) – Belaidė 4G kamera miškui, sodybai ar žvėrių stebėjimui be elektros ir Wi-FiNorite stebėti savo sodybą, miško teritoriją ar žvėrių lankomą vietą, bet nėra Wi-Fi ryšio ir elektros ti..
0
203
Gaisro apsauga gyvenamose patalpose: Ką atskleidžia statistika?Per pirmuosius keturis 2025 metų mėnesius Lietuvoje kilo net 33,8% daugiau gaisrų nei tuo pačiu laikotarpiu pernai Priešgaisrinės apsaugo..
0
432
Nokta Makro Legend yra pažangus, daugiadažnis metalo detektorius, sukurtas tiek pradedantiesiems, tiek patyrusiems lobių ieškotojams. Šis prietaisas išsiskiria moderniomis technologijomis, patogiu nau..
0
892
HIKMICRO: termovizoriai, naktinio matymo prietaisai, taikikliai ir priedėliaiHIKMICRO yra pasaulyje pripažintas termovizorių, naktinio matymo prietaisų, taikiklių ir priedėlių gamintojas, siūlantis au..
0
606
Palyginimas: GARMIN Alpha 200, Alpha 300 ir Alpha 300i – kuris sekimo įrenginys geriausiai tinka jūsų poreikiams?Jei esate medžiotojas ar aktyvus šunų augintojas, žinote, kaip svarbu turėti patikimą s..
0
357
GARMIN Alpha TT25 ir Alpha T20 – kuris antkaklis geriausiai tinka jūsų šuniui?Jei ieškote patikimo būdo sekti ir treniruoti savo šunį, GARMIN siūlo du pažangius sprendimus: Alpha TT25 ir Alpha T20 ant..
0
945
Jeigu galvojate, kad Jūsų namų interjeras yra tobulas ir bet kokie ant sienų sukabinti jutikliai jį sugadins, tai ši sistema kaip tik Jums. Šiuolaikiško ir modernaus dizaino jutikliai ne tik atrodys g..
0
11086
Kas yra AX PRO belaidė apsaugos sistema? AX PRO - tai neįtikėtinas naujas dizainas, kuris sujungia galingas ir patikimas praeities apsaugos sistemas su geriausių rytojaus technologijų paprastumu.AX PR..
0
7130
Pavogė REOLINK kamerą? Pristatome ką svarbu žinoti!Žingsniai:Atsidarę Reolink programėlę išmaniajame telefone, spaudžiate "Nustatymai".Spaudžiate ant kameros pavadinimo;Tuomet spaudžiate "Mobile Inf..
0
7355
Reolink GO 4G LTE atminties kortelės formatavimas...
0
4298
Reolink GO 4G LTE GMAIL email konfigūravimas, nuotraukų siuntimas..
0
2726
Prisijungimas prie Hikvision įrašymo įrenginio naudojant - InternetExplorerAtsidarome naršyklę Internet Explorer (Windows 10 vartotojai paskaitykite pastabą esančią instrukcijos pabaigoje). Adreso vie..
0
2336
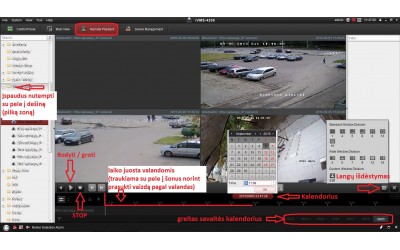
iVMS-4200 instaliavimo instrukcija1 žingsnis:2 žingsnis:3 žingsnis:4 žingsnis:5 žingsnis:6 žingsnis:7 žingsnis:8 žingsnis:9 žingsnis:10 žingsnis:11 žingsnis:12 žingsnis:13 žingsnis:14 žingsnis:15 žing..
0
1315
Šiame informaciniame straipsnyje parodysime kaip pasikeisti kamerų pavadinimus iVMS-4200 programinėje įrangoje. Reikia paminėti, kad pavadinimai čia pasikeičia tik Jūsų kompiuteryje esančioje prog..
0
2386
iVMS-4500 programos instaliavimas išmaniesiems įrenginiams1. Tarp visų programų susirandame Google Play parduotuvę (iPhone telefonuose analogiškai susirandame App Store parduotuvę). Ją atsidarę paiešk..





-400x250w.jpg)